Gaining More Control and Securing Your Network by Implementing Zero Trust Network
Throughout the last decades or so, network security is heavily reliant on the foundation of a strong, reliable firewall. However, with more sophisticated threats emerging, hybrid working trend and more workloads shifting to cloud, your traditional perimeter defense is no longer effective to protect your network.
This is where Zero Trust Network practices comes in.
What is Zero Trust ?
The concept of Zero Trust is nothing new and has been around for almost a decade. Zero Trust, at its core, is a security policy for your organization that removes traditional boundaries such as firewalls, routers and switches from being the only factor used to determine if a device is trusted or not.
With Zero Trust model, no device, user, or network segment is inherently trustworthy just because they are connected to your network. Zero Trust expects that
- Security threats can be inside or outside your network.
- Every device and person accessing resources on your network must be authenticated and authorized.
- By default, no person or device is trusted.
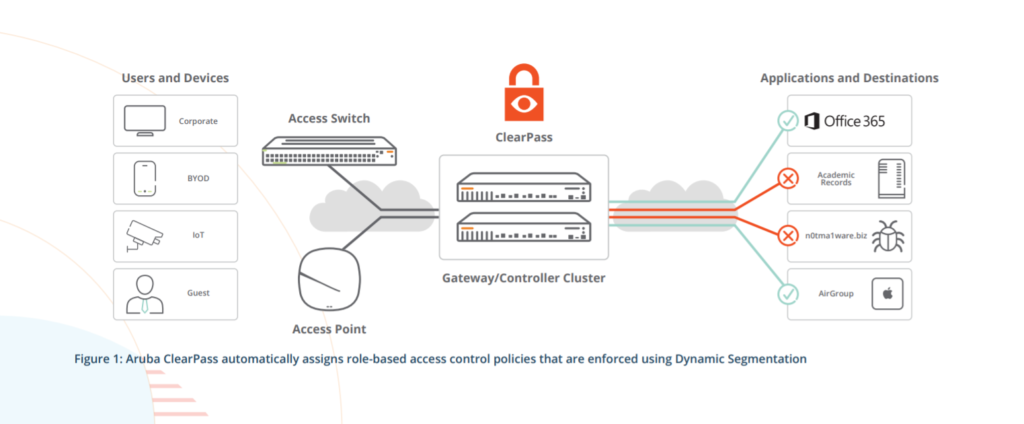
Although Zero Trust has a wide variety of definitions and applications, applying a Zero Trust approach to the network starts with user and device visibility combined with integrated identity-based access control. A complete Zero Trust Network must at all times grant you control and visibility so that IT can shorten the time spent on identifying and analyzing threats and be able to quickly respond and mitigate to risks in your network.
Aruba’s Zero Trust Security is designed around five core principles of Zero Trust: visibility, authentication, role-based access control, continuous monitoring and enforcement and response.

No one vendor or solution will deliver all the protection your organization needs. But, starting with strong, built-in network security means you have a head start on implementing a Zero Trust or SASE framework.
Aruba Zero Trust Security is built upon its ESP and Edge-to-Cloud Security framework. This security model incorporates comprehensive visibility, the least access micro segmentation and control, as well as continuous monitoring and enforcement across campus networks, branch networks, and extendable to home or remote workers.
To learn more about the principals of Zero Trust Networking, click on the “Download” button below. You may also request for a 1-to-1 presentation on this Zero Trust Networking by clicking on the “Schedule” button below.
Gaining More Control and Securing Your Network by Implementing Zero Trust Network
Throughout the last decades or so, network security is heavily reliant on the foundation of a strong, reliable firewall. However, with more sophisticated threats emerging, hybrid working trend and more workloads shifting to cloud, your traditional perimeter defense is no longer effective to protect your network.
This is where Zero Trust Network practices comes in.
What is Zero Trust ?
The concept of Zero Trust is nothing new and has been around for almost a decade. Zero Trust, at its core, is a security policy for your organization that removes traditional boundaries such as firewalls, routers and switches from being the only factor used to determine if a device is trusted or not.
With Zero Trust model, no device, user, or network segment is inherently trustworthy just because they are connected to your network. Zero Trust expects that
- Security threats can be inside or outside your network.
- Every device and person accessing resources on your network must be authenticated and authorized.
- By default, no person or device is trusted.
Although Zero Trust has a wide variety of definitions and applications, applying a Zero Trust approach to the network starts with user and device visibility combined with integrated identity-based access control. A complete Zero Trust Network must at all times grant you control and visibility so that IT can shorten the time spent on identifying and analyzing threats and be able to quickly respond and mitigate to risks in your network.
Aruba’s Zero Trust Security is designed around five core principles of Zero Trust: visibility, authentication, role-based access control, continuous monitoring and enforcement and response.

No one vendor or solution will deliver all the protection your organization needs. But, starting with strong, built-in network security means you have a head start on implementing a Zero Trust or SASE framework.
Aruba Zero Trust Security is built upon its ESP and Edge-to-Cloud Security framework. This security model incorporates comprehensive visibility, least access micro segmentation and control, as well as continuous monitoring and enforcement across campus networks, branch networks, and extendable to home or remote workers.

To learn more about the principals of Zero Trust Networking, click on the “Download” button below. You may also request for a 1-to-1 presentation on this Zero Trust Networking by clicking on the “Schedule” button below.




